Building a Solid Cybersecurity Foundation NACUSO Las Vegas April 4, 2016 PLATINUM PARTNER GOVERNANC E CYBER SECURITY POLICY FFIEC Risk Assessmen t RISK. - ppt download
Lesson 1-Introduction and Security Trends. Background Terrorists have targeted people and physical structures. – The average citizens are more likely. - ppt download

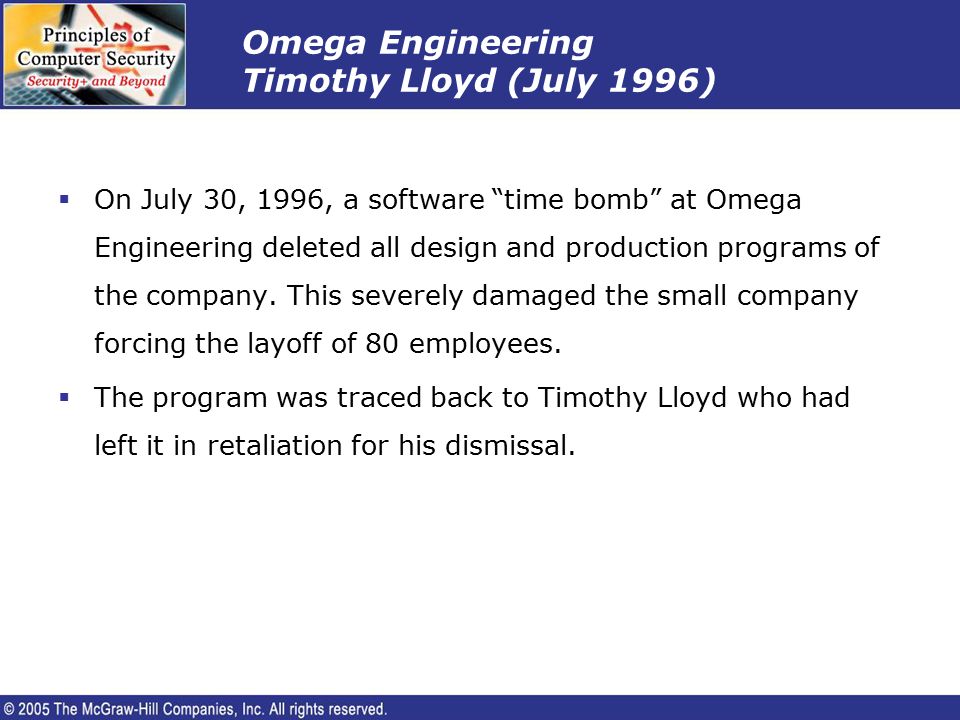
In the Tim Lloyd logic bomb attack on Omega Engineering, what type of vulnerability was the existence of the user "12345" an example of? | Homework.Study.com